Technology has become ingrained in our daily lives that it affects almost everything we do. Because of its impact, it is vital to touch on the topic of risk management in IT, and how RMM software can help mitigate it.
Hardware, software, applications and integrations need to adapt to ever-changing technology. Failure to keep up with the changes can result in errors or risks, affecting various facets of a business. To reduce this kind of outcome, you can use RMM risk management software.
Another challenge with IT is finding the right people which can resolve difficult issues. Companies need to find technicians or engineers with training and expertise in the field. They need to be dependable and willing to commit to responsibilities.
Steps on How to Manage IT Risks
Risk management is the application of the best practices in IT to handle the risks concerning that area. To do it, you need to assess the risks associated with the use of technology in an organization. Here are some tips on how you can manage risk with confidence.
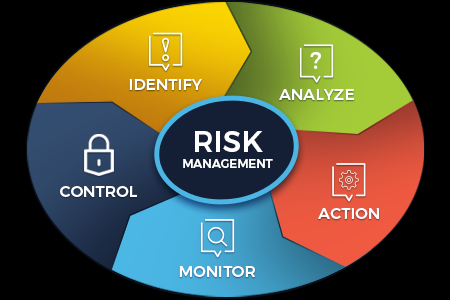
1. Determine the Risk
You can’t go to a fight unprepared. As such, you need to figure out first what are the problems or issues that may arise with the technology deployed in the organization. The leader and his team should always be ready to uncover and recognize risks, and explain how it could affect future projects and outcomes.
2. Analyze its Severity
Once you know the risks you’re going to face, you need to analyze the severity of its possible impact. Research about it and find out how this could influence your business processes. Include these findings on your assessment.
3. Rank its Priority
After analyzing the impact of risks, prioritize them according to their severity. Once you evaluate the potential impact of threats or failure, you can begin to develop strategies to control them. This way, you can ensure that the risks are addressed before they even fault the overall projects. These rankings will also be added to the risk assessment.
4. Respond to the Risk
If the risk ever becomes an actual problem, then you can no longer do anything to prevent it. Instead, you need to respond to it immediately. This is what’s commonly referred to as risk response planning, in which you prioritize high-risk issues and decide how to modify or treat them.
5. Monitor and Review the Risk
Make sure to keep an eye out on the progress of reducing the risks. Use RMM risk management tool to monitor and review how your team is dealing with the issue and the current health status of infrastructures to guarantee that nothing is left to chance.
How RMM Can Help Manage Risks
If an organization’s system experiences downtime, the consequences can be costly. Clients will be affected and they might lose faith in the company’s ability to deliver the services or products they need. In this situation, IT teams must put in place the necessary crisis strategies to mitigate or respond to risks.
Evaluate these risks early and often
Sometimes, organizations are not proactive enough. They only react once the risks happen. So, prior to starting a project or implementing conversions or integrations, think through and plan ahead of time to avoid downtime.
Apply necessary safeguards
This is a tactic for prevention, where the organization plans to reduce risk at all costs and relies on a lot of resources to that end. It is no longer a threat to the project if you can avoid the risk. You also get to dodge the related potential of its return if you place safeguards.
When you deploy RMM risk management software, you don’t only mitigate risks. You also take a proactive approach in terms of security risk management. It enables IT departments to install agents seamlessly onto remote IT networks, workstations, servers and other computing hardware that they are managing. This gives them the full visibility and management control, letting them receive important data such as health, status and performance. Through this, they can identify errors and issues remotely to resolve problems quickly and efficiently.